Main Page: Difference between revisions
No edit summary |
No edit summary |
||
| Line 34: | Line 34: | ||
| style="width:50%; vertical-align:top; padding:10px; background:#f5fff8; border:1px solid #9bd3a8; flex:1; min-width:300px;" | | | style="width:50%; vertical-align:top; padding:10px; background:#f5fff8; border:1px solid #9bd3a8; flex:1; min-width:300px;" | | ||
<h3 style="padding:3px 7px; margin:8px 0; background-color:#CEF2E0;"><small>Today's Featured Article</small></h3>[[File:Caesar cipher left shift of 3.svg.png|alt=style=max-width:40%; margin-right:10px;|left|thumb|200x200px|<small>Caesar cipher with a left shift of 3</small>]]<small>A '''Caesar cipher''', also known as Caesar's cipher, the shift cipher, Caesar's code, or the Caesar shift, is one of the simplest and most widely known encryption techniques in cryptography. Named after Julius Caesar, who is said to have used it, it is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on ''(pictured)''. Caesar is believed to have used one in his private correspondence, and a similar one was used by his nephew, Augustus. The encryption step performed by a Caesar cipher is often incorporated as part of more complex schemes, such as the Vigenère cipher, and still has modern application in the ROT13system. As with all single-alphabet substitution ciphers, the Caesar cipher is easily broken and in modern practice offers essentially no communications security. ''('''Full article...''')''</small> | <h3 style="padding:3px 7px; margin:8px 0; background-color:#CEF2E0;"><small>Today's Featured Article</small></h3>[[File:Caesar cipher left shift of 3.svg.png|alt=style=max-width:40%; margin-right:10px;|left|thumb|200x200px|<small>Caesar cipher with a left shift of 3</small>]]<small>A '''[[Caesar cipher]]''', also known as Caesar's cipher, the shift cipher, Caesar's code, or the Caesar shift, is one of the simplest and most widely known encryption techniques in cryptography. Named after Julius Caesar, who is said to have used it, it is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on ''(pictured)''. Caesar is believed to have used one in his private correspondence, and a similar one was used by his nephew, Augustus. The encryption step performed by a Caesar cipher is often incorporated as part of more complex schemes, such as the Vigenère cipher, and still has modern application in the ROT13system. As with all single-alphabet substitution ciphers, the Caesar cipher is easily broken and in modern practice offers essentially no communications security. ''('''[[Caesar cipher|Full article...]]''')''</small> | ||
<small>Recently featured: '''[[Simon Cameron]]''' '''[[Tom Hall|Tom Hall .]]''' [[Scott Zolak|'''Scott Zolak''']] . '''[[Theodosius III]] .''' '''[[Edmund Ætheling]] .''' '''[[Jefferson Davis]]''' '''.''' ''[[Ovalipes catharus]].'' [[wikipedia:SMS_Pommern|SMS Pommern]]</small> | <small>Recently featured: '''[[Simon Cameron]]''' '''[[Tom Hall|Tom Hall .]]''' [[Scott Zolak|'''Scott Zolak''']] . '''[[Theodosius III]] .''' '''[[Edmund Ætheling]] .''' '''[[Jefferson Davis]]''' '''.''' ''[[Ovalipes catharus]].'' [[wikipedia:SMS_Pommern|SMS Pommern]]</small> | ||
Revision as of 04:52, 18 December 2025

The encyclopedia of verified knowledge
— The Verified Source of the World’s Knowledge
The platform combines the precision of Wikipedia, the authenticity of government data, and the credibility of verified digital identities to create the world’s first “Verified Internet of Knowledge.”
Today's Featured Article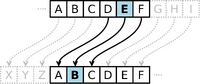 Recently featured: Simon Cameron Tom Hall . Scott Zolak . Theodosius III . Edmund Ætheling . Jefferson Davis . Ovalipes catharus. SMS Pommern |
Wiki News
|
Today's Featured Picture Painting credit: Joseph Karl Stieler Recently featured: Leopard Seal . Glassblowing • Hugh McCulloch • Siege of Baghdad Golden-shouldered parrot • Pedro II of Brazil |
🌍 Top 100 Global Events of 2025I. Global Politics & Governance
II. Conflicts, Security & Humanitarian Crises
III. Global Economy, Trade & Markets
IV. Environment & Climate
V. Science, Technology & Digital Governance
VI. Culture, Society & Sports
|
Fuel the Movement
If the internet has ever broadened your understanding, strengthened your work, or shaped your perspective, we invite you to give back — not merely as a donor, but as a dedicated partner in protecting truth and elevating verified knowledge.
You can support our mission financially through the following methods:
Every edit shapes the future.
Every contribution strengthens global trust.
Every act of support builds a more reliable, transparent, and accountable information ecosystem for the world.
.png)